Enterprise security and compliance in the top-rated scheduling automation platform
Scheduling automation without data security risks.
Table of contents
IT and security teams are constantly alert for security breaches. But the increasing frequency and sophistication of cyberattacks, phishing, and ransomware are intense. On top of that, there’s the new normal of a remote/hybrid workforce, who can sign up for SaaS apps in seconds. Add it up, and your team spends a lot of valuable time tracking down personal accounts to reduce risk.
We know you’d rather focus on strengthening your own infrastructure and security protocols. And as a top-ranked scheduling automation platform, we also know many of our millions of users already work at your company — many of whom have unconnected individual accounts.
As a scheduling automation platform in the business of making millions of connections happen seamlessly, Calendly understands the critical role security, privacy, and compliance play in this process.
Integrate secure enterprise scheduling with Calendly
Security threats evolve constantly. And so do Calendly’s protections, keeping your organization secure. Our Enterprise plan has robust security features and protocols that large organizations require.
The Enterprise plan provides the in-app security, compliance, and centralized administrative controls you need today, while Calendly’s committed security resources keep pace with tomorrow’s evolving threats. It’s no wonder that Sales, Marketing, Customer Success, Recruiting, and other teams rely on Calendly for Enterprise to close deals faster, retain customers, and schedule external meetings efficiently.
Collaborate without sacrificing control
People throughout your organization use productivity and collaboration tools to make their jobs easier. But team members using different, unconnected platforms for company projects create security risks. You have no visibility into who is using what tool or for what purpose. And when corporate IP gets siloed in private and/or personal app accounts, it’s impossible to control passwords and ensure other security protocols.
Data breaches happen almost every day, but keeping apps in one centrally managed account reduces your risk exposure. Calendly for Enterprise lets you consolidate personal accounts under one corporate umbrella, reducing risk without interrupting workflows. The plan’s enterprise-grade security and compliance features equip IT and security teams with more control over customer, employee, and business data.
Domain Control
With Domain Control, you can ensure employees signing up for Calendly join your primary, IT-managed account where they can access team integrations and features while complying with IT policies, such as single sign-on (SSO). Domain Control gives IT complete visibility into accounts associated with your domain, keeps corporate activity in one auditable location, and allows for more collaborative and efficient scheduling across your organization (instead of working in siloed accounts).
SAML single sign-on (SSO)
With SAML single sign-on (SSO), everyone in your company accesses Calendly with a single set of credentials that’s consistent with your identity provider. SSO helps you avoid weak passwords and gives admins greater control. It also makes employees’ lives easier, since they have fewer passwords to remember.
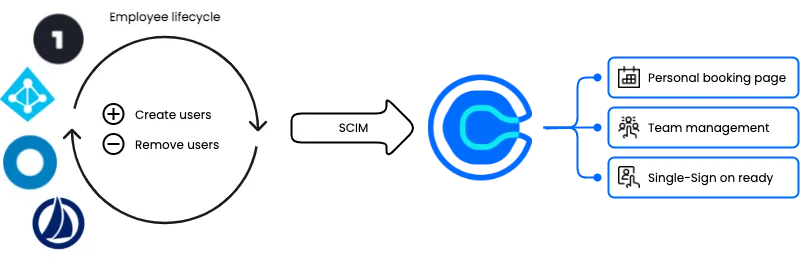
Advanced user provisioning
Meanwhile, integrating with your company directory to implement advanced user provisioning helps automate the Calendly user lifecycle and gets team members up and running quickly. Admins can onboard users to the company’s Calendly account through connections with identity providers like Okta, OneLogin, and Microsoft Azure. With SCIM enabled, employees are automatically removed from Calendly when they leave the company, saving admins time and reducing the risk of former employees retaining access. Your team can safeguard company IP and business data while simplifying user provisioning.
Automated group provisioning
When integrating with a company directory, leveraging Calendly’s SCIM functionality, IT and admins can onboard teams faster with group provisioning by automatically mapping new users to Groups in Calendly as they are provisioned into the account. IT and admins can determine how users are grouped based on predefined attributes like department, division, or location from your Identity Provider. As your organization scales, automated group provisioning continuously eliminates the manual process of assigning new users to groups.
“On the admin side, there is SCIM provisioning. You don't have to set up the user manually, just click the tile in your SSO. The barrier to entry is so low. The less work my IT team needs to do — and less work that the individual using the tool does — is where the benefits come in.”
Zlatko Unger
IT Director at Alation, Inc.
Administrative controls
IT and security teams don’t always oversee access to every application in your tech stack. And not every person should have the same level of access to your tools. Calendly for Enterprise features role-based access controls so you can assign different permissions for Calendly functions. For example, admins can manage all users, update meeting Event Type details for every team, delete data, and control billing tasks. Team managers can only manage users and Event Types within their own teams, while standard users can only edit their personal Event Types and settings. Admins also can distribute updates to all users at one time, so you know everyone’s using the newest version.
Enhanced group admin permissions
In line with making it easier to manage permissions even as your organization grows, IT can delegate management to group admins — giving them permissions to manage multiple groups of users at once without having to be a member of the group. Additionally, group admins can pull usage reports for their users, and create routing forms and managed events. Using the group admin role allows for departments within an organization to operate efficiently and independently.
“The security aspect of Calendly for Enterprise was important and the ease of deploying it out to the people that needed it. We got over a hundred licenses and it was really easy to set it up and deploy it out to the people.”
Procurement Manager
International media company
Calendly for Enterprise also provides IT and security teams with an activity log where they can monitor and quickly react to security incidents.
Your team can filter and analyze key account actions including logins, user invites, and changes to organizational settings within Calendly. All activity can be downloaded in a CSV file or integrated into your existing SIEM provider (via REST API). The activity log lets you quickly review events, understand changes, and identify potentially suspicious activity.
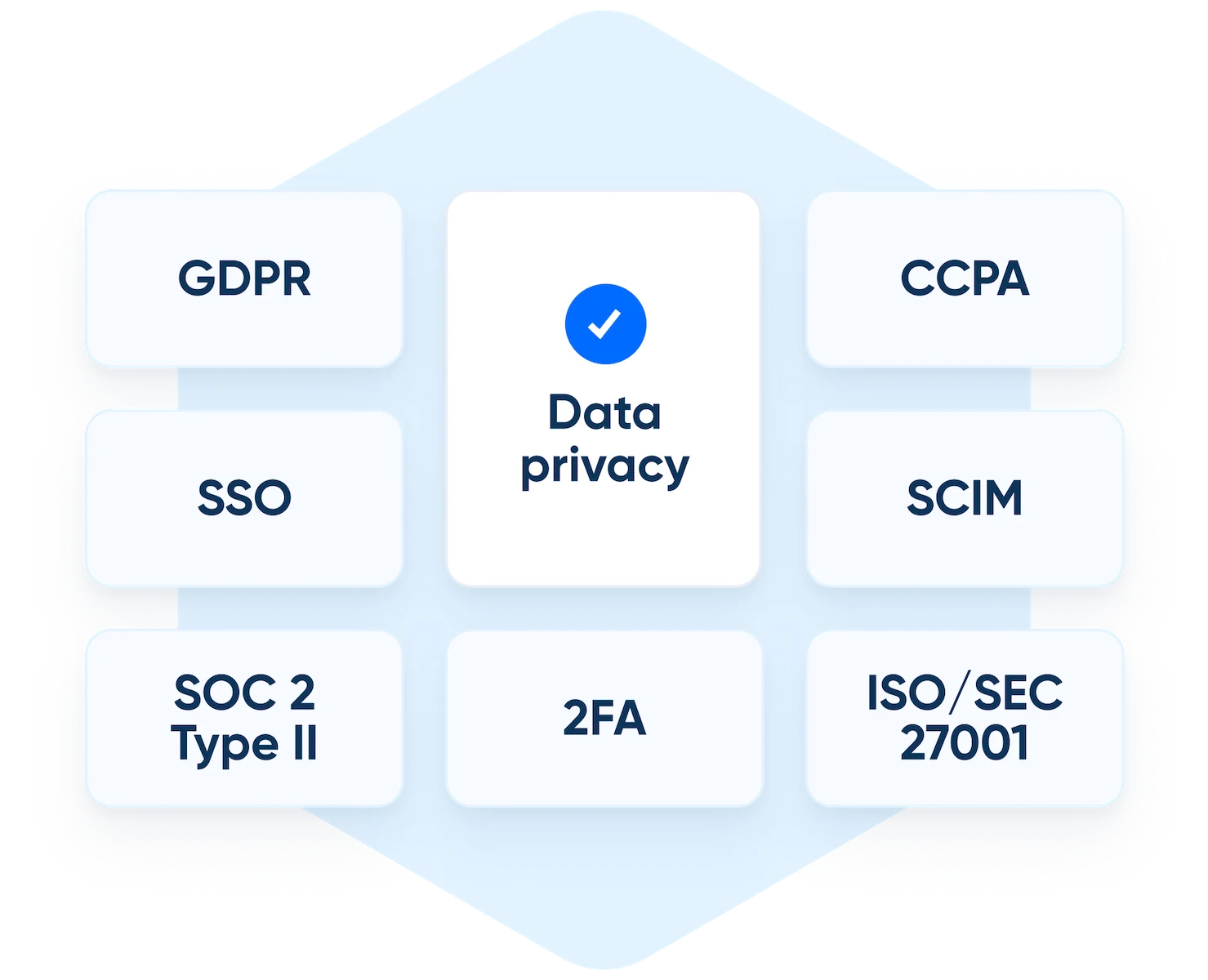
Align with data compliance standards and regulations
Enhancing security isn’t just about protecting your own networks. You also must protect customers’ data, and delete it on request. Some industries also have strict data auditing regulations.
Calendly for Enterprise not only aligns you with industry and global data compliance standards around the world. It also gives you the tools to complete data removal requests at scale, letting you find and delete customer data in one place. And Calendly is one of the few scheduling platforms that can create automatic backups of all communications, so you’re always prepared to audit when needed.
Recordkeeping compliance for financial services companies
Highly regulated industries like financial services must meet compliance requirements for client communications. It’s easy to stay compliant and be audit-ready with Calendly’s communication archiving capabilities.
With the Enterprise plan, Calendly creates a trackable, auditable record of all email and SMS communications sent from your account, including: meeting invitations, reminders, and follow-ups. Easily access your communications history at any time in your Activity Log and export your records via CSV and API.
Data privacy compliance
Customer data privacy protections have become a huge part of IT service requirements. The rise of regulations such as General Data Protection Regulation (GDPR), the California Consumer Privacy Act (CCPA), and other data privacy laws around the world mean customers have more control over how their personal data is used, including the “right to be forgotten.” When asked, you must delete their data from your systems promptly.
“Calendly goes above and beyond to publish their compliance information. That’s important to us, because having an official document from a vendor is considered a more accurate source of truth by our auditors than just an email from their CSM.”
Aaron Zander
Head of IT & Workplaces at HackerOne
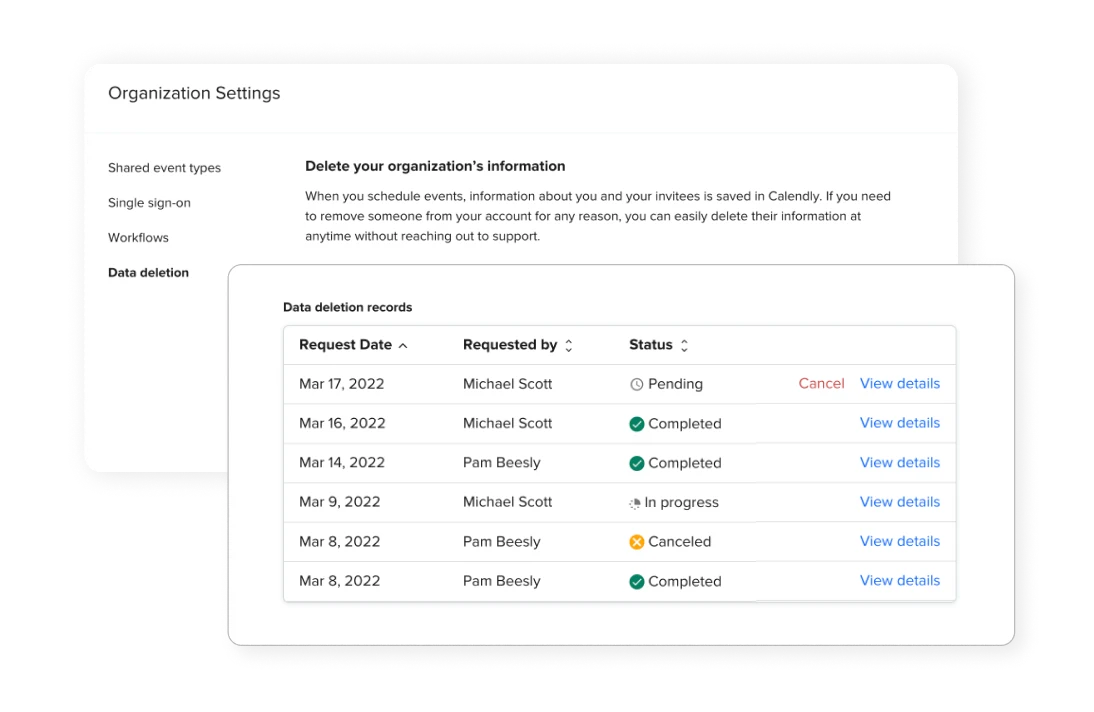
Overtasked IT teams shouldn’t have to jump through hoops to manage customer data. Fortunately, instead of manual one-off support requests, admins can initiate customer data removal with just a few clicks. The Enterprise plan takes customer privacy a step further with our Data Deletion API, which embeds Calendly’s data deletion feature in your existing deletion process. You can remove customer data, personally identifiable information (PII), and even accounts from one easily accessible location in your existing workflow.
Reinforce cybersecurity with a dedicated partner
As workflows get more complicated, software startups develop new apps to help people get more done. While these vendors may offer new and intuitive ways to work, security is often an afterthought.
Productivity shouldn't come at the expense of your network’s integrity. With Calendly, security is more than the features above. It includes our investments in people, protocols, and processes to integrate security measures into everything we do and be a responsive partner to your organization’s IT security team.
The State of Meetings 2024
24/7 trust and safety team
Trust and safety teams must provide security support at a moment’s notice. That’s why our security operations center is actively engaged in all aspects of our platform’s security. Our team is on guard against threats 24/7 and ready to respond to incidents immediately.
Internal security protocols and training
When everyone in your partner organization has a foundation in data security, it reduces the risks from threats outside your network. We create and maintain security programs and policies for all Calendly employees. Whether they work in IT or not, everyone receives continual training so they know how to avoid data leaks resulting from human error.
Secure software development lifecycle (SDLC)
Security checkpoints are also built into the way we develop new features:
Routine audits: We continuously scan for service interruptions, performance degradation, and security vulnerabilities.
New releases: Updated versions of Calendly require security tests, unit tests, integration tests, and end-to-end tests, as well as comparisons with our integration server.
Quality assurance testing: Changes are manually peer-reviewed by engineers, and then manually tested by our quality assurance team.
Continual monitoring: Following a release, we log, review, and address exceptions as well as conduct pen testing through multiple third-party services.
“We’re at a monumental moment in our history where people are mobile, hybrid work has become the norm, and workers have an endless number of devices at their disposal, meaning security leaders have a greater responsibility to usher customers and employees safely into this new era.”
Frank Russo
Chief Information Security Officer at Calendly
These are just a few examples of our dedication to security. More details are available on our security protocols and policies page.
Level up to Calendly for Enterprise
Your organization’s success depends on meeting and collaborating with people while keeping your network secure. It’s how everyone works more effectively, wins more customers, and grows revenue.
Calendly constantly updates and introduces new security features to keep your data — and your customers’ — safe. Consolidating your Calendly users in an Enterprise plan keeps everyone connected in a powerful, widely used scheduling platform with the security features and resources large organizations demand.
More than 100,000 organizations rely on Calendly’s secure scheduling to close deals, build relationships, and drive results — including Dropbox, Fidelity, Indiana University, Glassdoor, and L’Oreal. A study conducted by Forrester Consulting found that Calendly provided enterprise customers a 318% ROI over three years.
Contact us to learn what the Enterprise plan can do for you.
Learn more about Calendly
See how your organization — like thousands of others! — can use Calendly to increase revenue, accelerate sales pipeline, and improve customer retention.
Related Articles
Don't leave your prospects, customers, and candidates waiting
Calendly eliminates the scheduling back and forth and helps you hit goals faster. Get started in seconds.