Herramienta segura para millones de conexiones
Confíe en Calendly para mantener la seguridad de sus datos con una gestión administrativa de nivel empresarial, integraciones de seguridad, gobierno de datos, auditorías de cumplimiento y protecciones de privacidad.
Programación simplificada para más de
200,000,000 reuniones
El software líder en el mercado cumple con la seguridad de grado superior
Protección de datos del cliente
Separación lógica de inquilinos
Cifrado en tránsito (TLS 1.2+)
Cifrado en reposo (AES-256) y en tránsito
Seguridad de la infraestructura
Alojado en el proveedor líder de infraestructura en la nube
Protección de red y perimetral
Protección de aplicaciones
cortafuegos de aplicaciones web
Protecciones de denegación de servicio distribuida (DDoS)
Escaneo regular de vulnerabilidades
Prueba semestral de penetración
Cumplimiento y privacidad
Informe SOC 2 de tipo 2
Informe SOC 3
Gestión del cumplimiento del RGPD & CCPA
Certificación CSA STAR de nivel 1
Seguridad empresarial
Formación de concienciación y educación de seguridad
Supervisión las 24 h y respuesta ante incidentes
Gestión de riesgos del proveedor
Planificación de la continuidad empresarial
Protección de cuenta
Prevención de bots
Notificaciones de inicio de sesión
Gestión de ciclos de vida de SSO y usuario (SCIM)
Registro de actividad en tiempo real (auditoría)
Gestión de eliminación de los datos de identificación personal
Solicitar documentación a través de Whistic
Calendly utiliza Whistic para compartir de forma segura los perfiles de seguridad de las empresas y los productos, así como la documentación detallada necesaria para las evaluaciones de seguridad de los proveedores.
Certificaciones y marcos de trabajo
Adáptate a las necesidades comerciales en evolución, sin el riesgo
Seguridad a escala
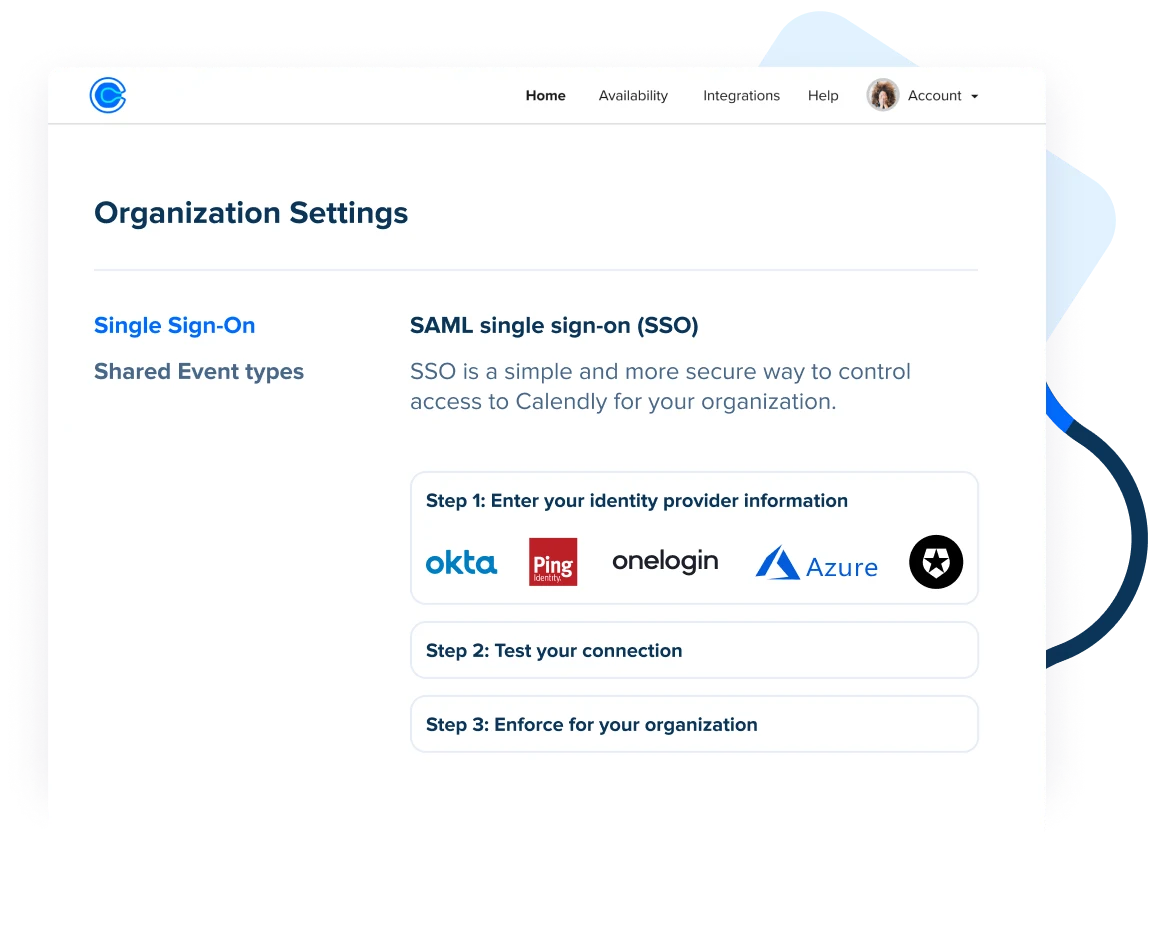
¿Más personas? No pasa nada. Integre herramientas flexibles de gestión de acceso, incluyendo SSO, SCIM, un registro de actividad y mucho más, en sus políticas corporativas y flujos de trabajo informático para no pasar nada por alto.
Control de dominios y protección de datos
Reclama tu dominio corporativo y establece cómo los nuevos empleados que se inscriben en Calendly solicitan acceso a tu cuenta centralizada y gestionada por Tecnología de la Información
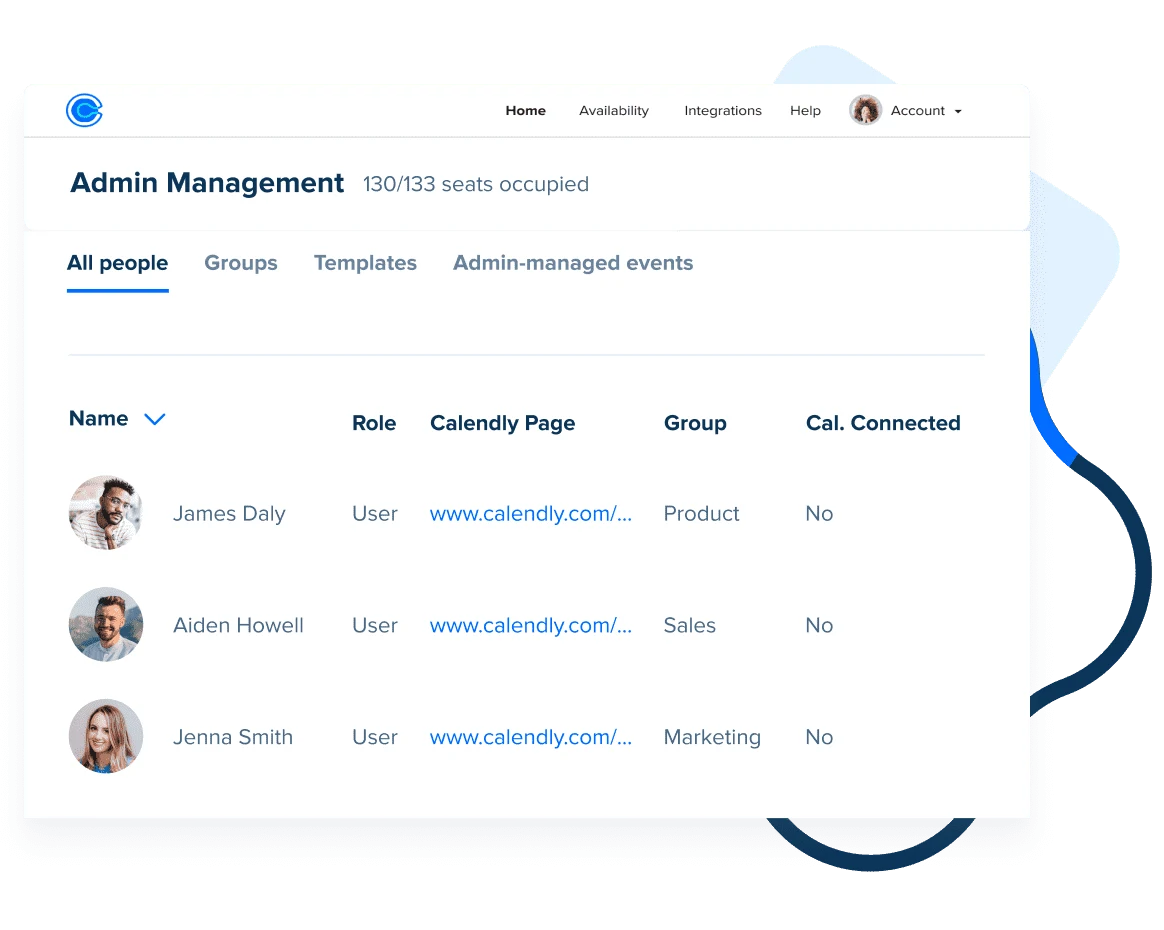
Colaboración con control
Capacite a sus empleados para que puedan programar eficientemente como un equipo sin añadir riesgos para el negocio. El registro de la actividad (auditoría) de Calendly ofrece visibilidad mientras que los permisos basados en los cargos laborales previenen cambios no autorizados.
Gobernanza de datos de grado empresarial
Garantice el cumplimiento de las capacidades de gobernanza y gestión de riesgos de Calendly, como políticas de retención global, condiciones de servicio personalizadas, eliminación de datos, seguimiento de auditorías y mucho más.
Fraud, confianza y seguridad
La seguridad y la protección de los datos de los clientes no deberían ser una idea de última hora. El equipo especializado de Calendly mejora constantemente nuestras técnicas de seguridad y aborda la suplantación de identidad, el fraude y otras actividades sospechosas.
“El aspecto de la seguridad de Calendly para la empresa fue muy importante, al igual que la facilidad de implementarlo para las personas que lo necesitaban. Obtuvimos más de cien licencias y fue realmente fácil configurarlas e implementarlas para todos”.
Recursos adicionales
Acceso fácil para reservas fáciles
Comparta su enlace de Calendly directamente desde su navegador, para que pueda programar reuniones sin tener que cambiar de pestaña.